Understanding of security operations
Compare security operations with security operations and maintenance
Operation and maintenance: In short, operation and maintenance is to ensure the normal operation of the information system, so that it can be used normally according to the design requirements, and to provide higher quality services through technical guarantee products. [2]
Security operation and maintenance = security + operation and maintenance
Operation: Operation must continuously output value. [2] This description is very broad, but it can well describe the overall role of operations students.
Security Operations = Security + Operations = Produce valuable security information through existing security systems and tools, and use it to solve security risks to achieve the ultimate goal of security. [2]
Opinions of industry experts
-
Jun Ge’s article "How Enterprises Build an Effective Security Operation System" [3] mentions what security operations are, and there are several points in it:
-
The means are not the ends, and safety capabilities and safety knowledge do not completely represent the safety level.
-
In most cases, companies pay for output, not for knowledge. Therefore, someone needs to analyze and diagnose the problem. After discovering the crux, coordinate resources to ultimately achieve the goal.
-
Profession owes money: In order to achieve safety goals, the process of proposing safety solution ideas, verifying effects, analyzing problems, diagnosing problems, coordinating resources to solve problems, and continuing iterative optimization
- Lake2: Security personnel use security systems to formulate security policies and promote the process of resolving security risks, which is security operations.
- Qin Bo: Safety operation is the control of risks and the pursuit of a balance between safety investment returns and risks.
Interpret the recruitment job description
Bytedance’s official recruitment requirements
Job description
- Be familiar with the common cheating techniques used by illegal companies, be able to identify cheating risks in business logic, and promote the implementation of solutions;
- Conduct an in-depth analysis of the black and gray industry chains involving the platform, restore the links of techniques, mine characteristics, and link up with the police to crack down on black and gray industries offline;
- Have an in-depth understanding of business risks and have the ability to discover clues, analyze data, investigate and collect evidence, and coordinate disposal;
- Able to independently undertake special analysis work for business lines, output analysis reports, strategic models or other data product results and follow up on implementation. Job requirements
- Bachelor degree or above, majoring in computer or information security, those with PMP related certificates are preferred;
- Have experience in anti-cheating, anti-crawling and other security-related fields, and be familiar with the operation mode of black industry chains and various cheating methods. Applicants with experience in risk control product operations and data analysis will be given priority;
- Good at data analysis, sensitive to data, able to accurately describe and identify cheating characteristics, and good at discovering valuable key points from large amounts of information;
- Have good communication and coordination skills, strong analytical skills, process management skills, rich experience in cross-team cooperation, and strong execution ability. Refer: https://www.anquanke.com/post/id/194958
Analysis from seniors
I am very grateful to Senior W for his patient answer to me. I have summarized the job requirements explained by Senior W. The main points are as follows.
-
on the whole I think it's a broad range of emergency engineers But I will follow it more deeply This job definitely requires experience But since we are recruiting interns Then the experience requirements shouldn’t be too high. You can focus on demonstrating your emergency capabilities
-
Mainly likely to be emergency response efforts In fact, I don’t do much in emergencies. You can read more cases
-
You can prepare cases of data analysis in actual emergencies You can prepare several cases where you analyzed data in actual emergencies The more interesting ones are the best
-
To test analytical skills I think this should test the interviewer’s analytical skills. Knowledge accumulation can be achieved quickly Coherence and sensitivity of thinking There should also be some report writing work There may be development and modeling work For example, automatic analysis platform (this happens to be the educational big data analysis and application platform I work on, and it is also written on my resume)
-
What preparations are needed in terms of analytical capabilities? I think we just need to understand the characteristics. For example, attack packet characteristics Threat intelligence There are also process abnormal characteristics -- The most important thing is to show your coherent thinking about an event Discover something from something Such a derivation process is analysis
-
You need to know something about black industry Then we can also understand some of the methods of black production. Possible traces of black production Gambling blackmail Mining
Analysis from Teacher Q
Mainly doing research on black and ash production There are more scams on Douyin Use an older QQ account to join many black industry groups (QQ groups to search for online earning, harvesting wool) and obtain real-time information Douyin is a black and gray product, brushing up volume, brushing up on registrations, brushing up likes and fans, cheating in business In terms of advertising, it was normal when uploaded, but later changed to gray and black, advertising hijacking. Not particularly relevant to emergency response Be very familiar with the gray and black chains To analyze this, we need to completely restore the chain from a black and gray production clue. In terms of cases, for example, Guo Shenghua diverted traffic from Douyin to QQ groups, sales courses, etc. Social work skills are required
Introduction from Master A
Master A works in Toutiao. His main advice is
This traceability is different from the traceability of Party B’s emergency response Mainly anti-climbing and risk control Anti-climbing and tracing back to the source Human-machine recognition Cluster analysis 2. Have working experience in anti-cheating, anti-crawling and other security-related fields, and be familiar with the operation mode of black product chains and various cheating methods. Applicants with experience in risk control product operation will be given priority; 3. Have a keen eye for data, be able to accurately describe and identify cheating characteristics, and be good at discovering valuable key points from large amounts of information. Looking at the business, the black products of e-commerce There are more wool party members Toutiao’s main consideration is video copyright So crawlers are very important
From Master L
Question: What is security operations? What is the difference between security operation and maintenance?
It can be roughly understood as the difference between operation and operation and maintenance: Operation is the continuous operation and maintenance of the system, analyzing the operation status and generated data, finding problems and improving optimization; operation and maintenance is the release, update and maintenance of the system. Regarding security operations, you can search for the trilogy "Careers owe money and talk about security operations" (not this name, you have to search "Careers owe money, security operations", I helped him pick this name) and Nie Jun's articles on security operations. In addition, I plan to write about security operations in the next article.
Operation is the continuous operation and maintenance of the system, analysis of operation conditions and generated data, discovery of problems, improvement and optimization
From 360 Security Operation Engineer
This part comes from the introduction of the "Growth Path of Network Security Operations Engineer" course at 360 Network Security University: Link
Growth Roadmap
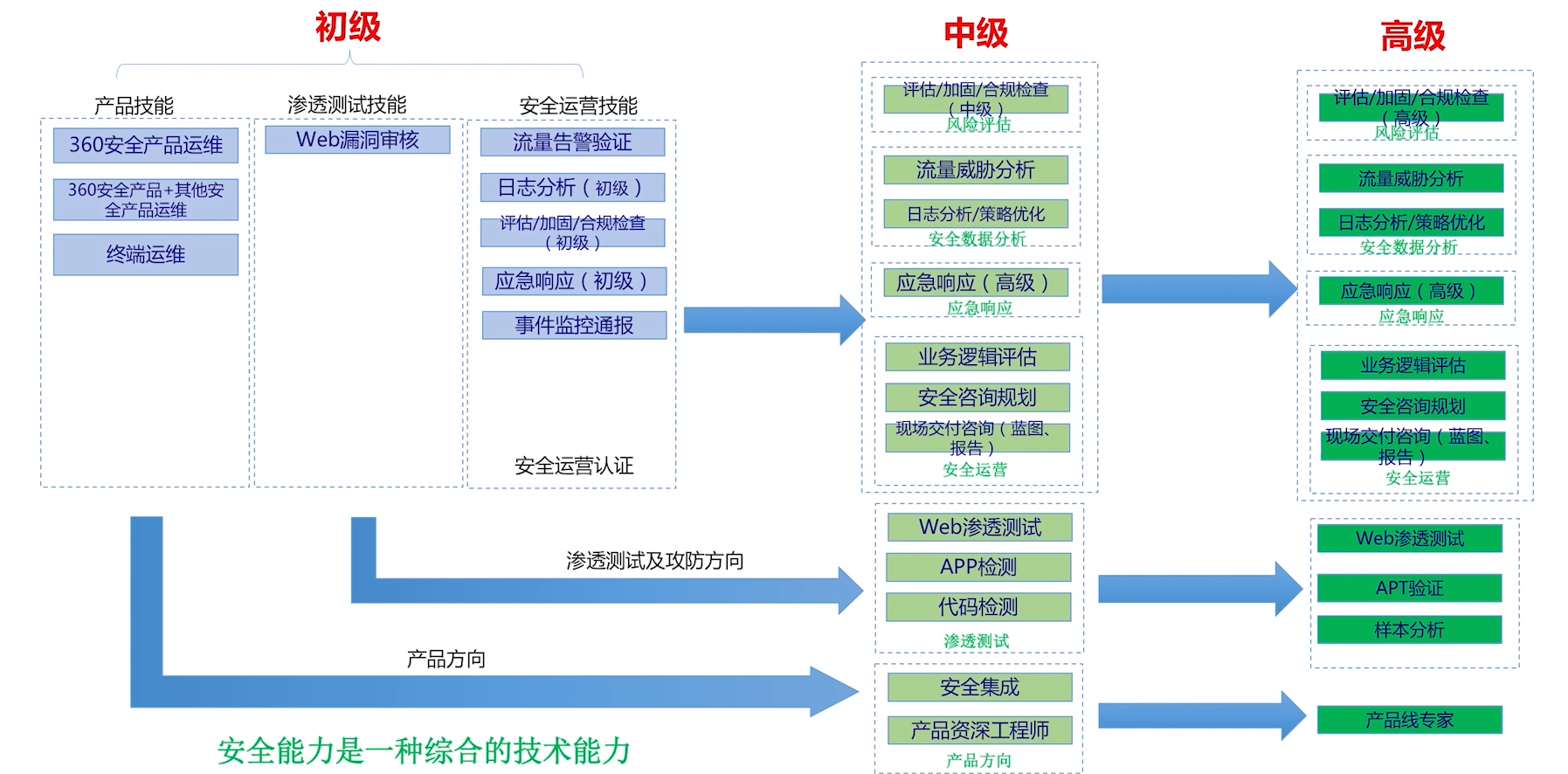
References
[1] Xingshuo · Looking at security operations from the perspective of data analysis, in-depth exploration of attack effectiveness verification, Xingshuo security operations, https://mp.weixin.qq.com/s?__biz=MzUxNDcyOTQxOQ==&mid=2247484052&idx=1&sn= 8d637125280cd5cb52529faf2f9bb797
[2] Security Operations: Solving the “Last Mile of Security”, Ma Jiangbo, General Manager of Big Data and Security Operations Division of Qi’anxin Group, https://www.secrss.com/articles/13864
[3] How enterprises build an effective security operation system, Brother Jun, https://static.anquanke.com/download/b/security-geek-2019-q3/article-1.html